Introduction
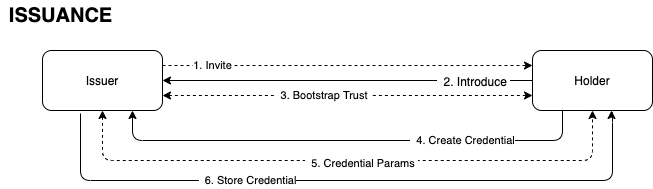
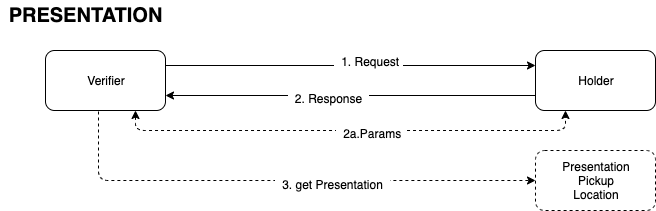
The objective of this specification is to define a common, minimalist message protocol for Issuers, Holders and Verifiers for the purpose of requesting and exchanging W3C Verifiable Credentials and Presentations across technology boundaries.
This protocol is meant to be transport agnostic; certainly it must operate in Web based scenarios, but it also must be compatible in offline (sometimes even connection-less) scenarios. Therefore this specification will first define the messages, and then later in the document various bindings will be defined.
There are currently multiple standard (and developing standard) protocols for facilitating the actual transfer of Verifiable Credential data, for example Aries DIDComm and the Credential Handler API (CHAPI), and more popular frameworks like OAuth and OpenID Connect may also be used. Most of these protocols provide a high degree of flexibility in their message structure, making them useful beyond Verifiable Credentials. This protocol will therefore treat these generic transfer technologies as Communication Channels - or 'pipes' for facilitating message transfer. This will allow developers to build Verifiable Credential based systems in a way that they are guaranteed some level of interoperability decoupled from more feature rich protocols and technology stacks.
The goal of this specification is to define a common message structure so that Issuers, Holders, and Verifiers can exchange Verifiable Credentials across these Comm Channels: entities using the same Comm Channel can operate over that channel, and entities integrated to different channels may rely on 'adapter' software to pass these messages across those channels; and still process the request/response to exchange credentials. Sessions may even initiate on one channel and transfer to another during the course of the communication.
This protocol takes into account and aims to be interoperable with the following:
- Verifiable Credentials v1.0 proof formats: LD-Signatures, ZKP, and JWS.
- Credential Handler API browser extension.
- Hyperledger Aries DIDComm.
- OAuth "3" transactional authorization.
- Blockcert ...?
- did:key method.
- did:peer method.
- JSON Web suite of specifications (JW*), including JWM ?
- DID Resolver protocol.
- ISO/IEC TC JTC1/SC 17 N Mobile Drivers license specification.
Out of scope for this specification are the details of how various technologies make use of Encrypted Data Vaults, message routing or proxying, multi-party (3+) extensions, and Verifiable Presentation privacy considerations (unless they are part of the message structure).
Note it is also possible that during the course of this messaging entities may determine they cannot interoperate due to the nature of the schemas and formats of the Verifiable Credentials being exchanged; this is an unfortunate but acceptable outcome. For example, a Holder simply may not have the Credentials matching the requested Schema by the Verifier. The Issuer may not be able to support a particular signing algorithm required by the Holder. C'est la vie.
Layering
This protocol specification is meant to sit atop the Verifiable Credentials v1.0 data format, the various Communication technologies and the transport layers. The following diagram is a visual (but not exhaustive) representation of how the various components in a Decentralized Identity ecosystem fit. Your mileage may vary.
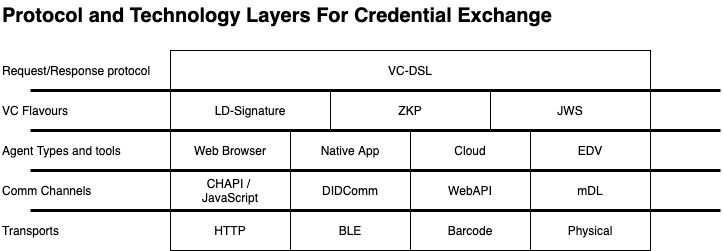
When the protocol can be used in conjunction with a particular message transport technology, this is referred to as a binding. Sample bindings are included in the Annex, and may be expressed as separate specifications.